Secure Your Smart Home: Free SSH Router And IoT Setup Explained
Keeping your smart home gadgets and router safe from prying eyes is, you know, a really big deal these days. With so many devices connected to the internet, from your smart lights to your security cameras, making sure they are protected is pretty much essential. This guide is all about showing you how to set up SSH on your router and IoT devices without spending a dime, giving you a powerful, free way to keep things secure and accessible from wherever you are. We'll talk about how this kind of setup works and why it's a good idea for anyone with a connected home, so it's a pretty useful thing to know.
People often wonder about getting into their home network from far away, or maybe they just want to make sure their internet-connected things are as locked down as possible. Sometimes, it feels a bit tricky to figure out where to start with all the tech talk, but honestly, it's not as hard as it seems. We're going to break down the process for you, step by step, making it clear and simple, which is rather nice. This way, you can feel more in control of your digital space and have peace of mind about your devices, so that's a plus.
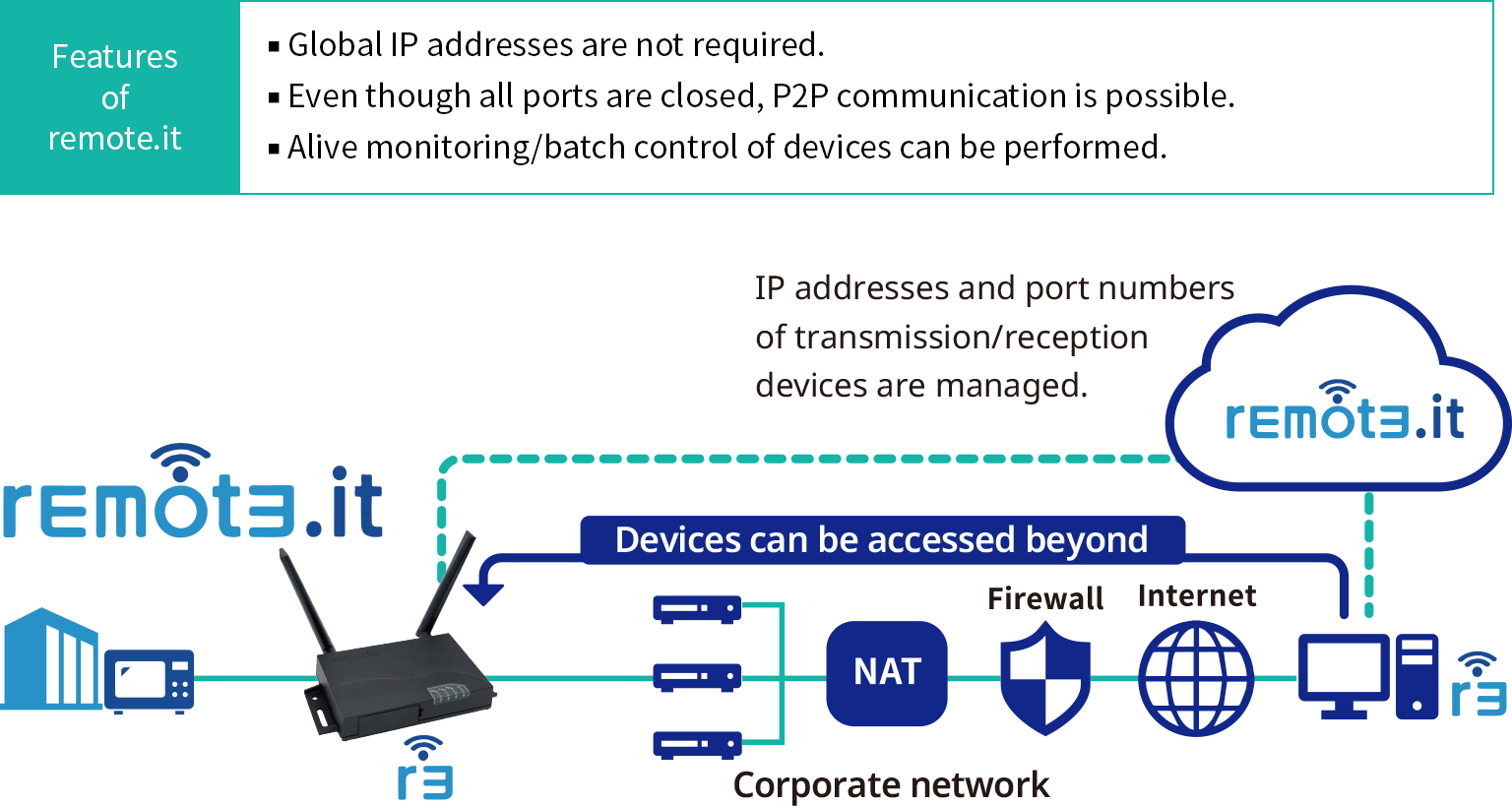
Think about all the cool stuff you can do when you have secure remote access to your router and IoT devices. You could check on your home while you're out, update software on a smart device, or even fix a small issue without being physically there. It gives you a lot of freedom and, too it's almost, a kind of superpower over your home network. This whole idea of using SSH for this purpose is quite popular because it's known for being very secure and, well, pretty reliable, which is what we all want, right?
Table of Contents
- Why SSH for Your IoT and Router?
- Getting Started: Your Free SSH Setup
- Boosting Security with SSH Keypairs
- Graphical Access and X11 Forwarding
- Common SSH Challenges and Solutions
- Frequently Asked Questions
- Final Thoughts on Your Secure Setup
Why SSH for Your IoT and Router?
So, why would you even consider using SSH for your home router or those smart devices you have? Well, it's pretty simple, actually. SSH, which stands for Secure Shell, is a way to get into a computer or device from far away, but it does so in a very private and protected manner. It creates a kind of secure tunnel for your information, so nobody can snoop on what you are doing or what you are sending. This is a big deal when you are talking about devices that are always connected to the internet, so that's a key reason.
A lot of people worry about the privacy of their smart home things, and quite rightly so. When you set up SSH, you are basically adding a strong lock to your digital front door. It helps keep unwanted visitors out and makes sure only you, or someone you trust, can get in. This kind of protection is, you know, just what you need in a world where everything seems to be online. It's a free solution, too, which is a nice bonus for anyone looking to boost their home network's safety without spending extra cash.
Security First: Why SSH Matters
When you think about security for your internet-connected devices, SSH really stands out. It's designed from the ground up to be a very safe way to communicate. It uses strong methods to make sure your data is scrambled and can't be read by just anyone. This is especially important for things like your router, which is basically the gateway to your entire home network. If someone gets into your router, they could potentially get into everything else, so keeping it locked down is super important, you know?
- William Devane Bio
- Family Rickey Smiley Wife Krystal
- Kylie Bbl
- Alice Rosenblum Age
- Bts Members Names And Roles
For IoT devices, which might not always have the best built-in security, adding SSH can give you an extra layer of protection. Many of these devices, you see, might use simple passwords or have open ports that are easy targets. By setting up SSH, you are putting a much tougher barrier in place. This helps prevent bad actors from taking control of your smart thermostat or your security camera, which is, honestly, a pretty scary thought for most people.
Remote Access, Simplified
Beyond security, SSH makes getting to your devices from anywhere really straightforward. Imagine you are away from home and you need to restart your router, or maybe check a log file on your smart hub. With SSH set up, you can do this from your laptop or even your phone, as a matter of fact. It means you don't have to be physically there to manage your home network, which is very convenient for busy people or those who travel a lot.
It's also a great way to handle updates or troubleshoot problems on your IoT gadgets. Instead of having to physically unplug something or connect it to another computer, you can just log in through SSH and run commands. This saves a lot of time and effort, and honestly, it just makes managing your connected home a lot easier. It's a pretty practical tool for anyone who likes to have full control over their tech, so it's worth learning about.
Getting Started: Your Free SSH Setup
Alright, let's get into how you can actually set this up for yourself. The good news is that for many devices, a lot of the basic parts are already there, or they are pretty simple to add. We're aiming for a free setup here, so we'll be using tools that are widely available and don't cost anything. It's about making smart choices with what's already out there, you know, for everyone to use.
The first step is often just checking what your devices can already do. Some routers, especially those running custom firmware like OpenWrt, come with SSH built right in. Many Linux-based IoT devices also have SSH ready to go. This makes the starting point much simpler, as you might only need to turn it on or change a few settings, which is pretty handy.
Checking for SSH on Your Devices
Before you do anything else, you'll want to see if your router or IoT device already has SSH enabled or if it's an option you can turn on. You can usually find this in the device's web interface under settings like "Administration," "Security," or "Remote Access." Look for something that says "SSH Server" or "Enable SSH." Sometimes, it's just a little checkbox you need to tick, which is fairly easy.
If you are trying to connect to a device and you're not sure if SSH is running, you can try to connect to it using a standard SSH client. If you get a connection refused message, it probably means SSH isn't active or isn't listening on the default port. But if you get a password prompt, then you know it's working, and that's a good sign, obviously.
Basic Server-Side Setup
Once you confirm SSH is available, you might want to make a few tweaks on the device itself. This is often called the "server-side" setup, because your router or IoT gadget is acting as the SSH server that you will connect to. These changes can make your connection more secure or simply make it work better for your specific needs, which is pretty useful.
A very common and highly recommended step is to change the default port that SSH listens on. By default, SSH usually uses port 22. But, you know, a lot of automated attacks out there will try to hit port 22. Changing it to something else, like port 5643, can significantly reduce the amount of unwanted traffic trying to get into your device. It's like moving your front door to a less obvious spot, so it's a bit safer.
Changing the Default SSH Port
To change the SSH port on a Linux-based system, which many routers and IoT devices run, you might edit a configuration file. For instance, some systems use a socket configuration. We've seen situations where, after editing a file like `systemctl edit ssh.socket`, and adding `listenstream=5643` under the `[socket]` section, then running `systemctl restart ssh.socket`, we were able to connect to SSH using the new port. This kind of change helps keep your device a bit more hidden from automated scans, which is a really good thing for security, actually.
Always remember to save your changes and then restart the SSH service or the device itself for the new port setting to take effect. If you don't restart the service, the old port might still be in use, or the new one won't activate, which would be, you know, a bit frustrating. This step is a simple but effective way to boost your device's protection against common attacks, so it's worth doing.
Understanding MAC Algorithms
Another aspect of SSH security involves what are called MAC algorithms. MAC stands for Message Authentication Code, and these algorithms make sure that the data being sent back and forth hasn't been tampered with. The list of supported MAC algorithms is determined by an option called `macs`, which you can find in both `ssh_config` (for the client) and `sshd_config` (for the server). If this option is not set, the system uses its default list, which is usually fine.
However, if you want to make your connection even more secure, or if you are having trouble connecting due to older or newer security standards, you might want to change the value for the `macs` option. This lets you specify exactly which algorithms your SSH connection will use. It's a bit more advanced, but knowing about it can help you fine-tune your security settings, which is pretty cool for those who like to tinker.
Client-Side Connections: What You Need
Now, for connecting to your device, you'll need an SSH client. The good news is that most operating systems already have one built-in, or they are very easy to get for free. For example, many people are accustomed to using PuTTY on a Windows computer, or just the command line terminal on an OSX machine, to SSH into something like a network-attached storage device. Often, you don't even need to do any special setup of the client itself, which is very convenient.
On Linux and macOS, you can just open your terminal application and type `ssh username@ip_address`. For Windows, PuTTY is a popular choice, and it's a free download. These tools let you tell your computer to connect to your router or IoT device using SSH, and they handle all the tricky parts of making that secure connection. It's pretty straightforward once you get the hang of it, you know?
Boosting Security with SSH Keypairs
While using a password for SSH is okay, using SSH keypairs is a much, much safer way to go. A keypair consists of two parts: a private key, which you keep secret on your computer, and a public key, which you put on the device you want to connect to. When you try to connect, the two keys talk to each other to prove who you are, without ever sending your password over the network, which is very secure.
This method is highly recommended for any device you want to access remotely, especially your router or IoT gadgets. It pretty much eliminates the risk of someone guessing your password, and it makes automated login much simpler and safer. It's a free way to really step up your security game, so it's something you should definitely consider setting up.
Creating Your SSH Keypair
Making an SSH keypair is quite simple. On Linux and macOS, you open your terminal and type `ssh-keygen`. It will ask you where to save the keys and if you want a passphrase. A passphrase adds another layer of security to your private key, which is a good idea. For Windows users, PuTTYgen is the tool you'd use to create these keys, and it works in a similar way, so it's not too different.
Once you have your keys, you'll need to copy the public key to the device you want to connect to. This usually goes into a file named `authorized_keys` inside a hidden directory called `.ssh` in the user's home directory on the remote device. This step is crucial for the key-based authentication to work, and it's fairly easy to do with a command like `ssh-copy-id` or by just manually pasting the key, you know.
Using Custom Keys and Directories
Sometimes, you might need to connect to a specific server using an SSH keypair that you created just for that purpose, not your usual `id_rsa` keypair. For instance, if you need to connect to an SSH proxy server with a unique key, you can specify which private key file to use when you run the `ssh` command. You would use the `-i` option followed by the path to your private key file, like `ssh -i /path/to/your/custom_key username@server`.
It's also worth noting that the `.ssh` directory is not always created by default below your home directory when you first start using SSH. When you call `ssh somehost` (replacing 'somehost' with the name or IP of a host running SSHD), the system often creates this directory for you. However, if it's not there, you might need to create it yourself and set the correct permissions, which is pretty simple to do with commands like `mkdir ~/.ssh` and `chmod 700 ~/.ssh`, so that's something to keep in mind.
Automating Tasks with SSH Keys
One of the really powerful things about using SSH keys is how easy they make it to automate tasks. Imagine you want to create a bash script from one server that will execute some commands on another server via SSH. With key-based authentication, you don't need to manually type a password every time the script runs, which is incredibly useful for scheduled jobs or continuous operations.
For example, if you need to SSH to server 2 using your private key file from server 1, your script can simply include the `ssh -i /path/to/private_key user@server2 'command_to_run'`. This is also very handy for scripting in other languages like Python. We've seen people writing scripts to automate command line commands in Python, doing calls like `cmd = "some unix command"`, where the SSH part is handled smoothly because of the pre-set key authentication. This makes managing multiple devices a breeze, honestly.
Graphical Access and X11 Forwarding
Sometimes, you might want to access a graphical user interface (GUI) on your remote device, not just the command line. This is where X11 forwarding comes into play. It lets you run graphical programs on your remote router or IoT device, and have their display appear on your local computer. It's a bit like having a remote desktop, but specifically for individual applications, which is quite useful for certain tasks.
This is especially helpful if your router or IoT device has a lightweight GUI you prefer to use, or if you need to run a graphical tool for configuration or troubleshooting. It means you don't have to install a full remote desktop solution, which can be heavier on resources. It's a pretty neat trick for those who prefer visual interfaces, so it's worth knowing about.
What is X11 Forwarding?
X11 forwarding is a feature of SSH that allows graphical applications running on a remote machine to display their windows on your local machine. When you run SSH with X11 forwarding enabled, it creates a secure channel for the display data. If you run SSH and your display is not set, it means SSH is not forwarding the X11 connection, which can be a bit confusing at first.
To confirm that SSH is forwarding X11, you can check for a line containing "requesting X11 forwarding" in the output when you connect with SSH in verbose mode (using `ssh -v`). This line tells you that the request was made. If you don't see it, or if you get errors about the display, then the forwarding isn't happening, and you'll need to check your SSH client and server settings, which is pretty important.
Setting Up for Remote GUI
To get graphical access over SSH, you usually need to enable X11 forwarding on both the SSH client and the SSH server. On the client side, you typically use the `-X` or `-Y` option with the `ssh` command (e.g., `ssh -X username@ip_address`). On the server side, you need to make sure `X11Forwarding yes` is set in the `sshd_config` file, and then restart the SSH daemon.
For instance, if you're trying to figure out a lightweight way to configure your Ubuntu 16.04 LTS server to have access via GUI over SSH, you'd want to make sure these settings are in place. Then, from your Ubuntu 16.04 workstation, you could connect with `ssh -X` and run a graphical application, and its window would appear on your workstation. It's a very convenient way to get a visual interface without a lot of extra setup, so it's a popular choice.
Troubleshooting X11 Display Issues
Sometimes, X11 forwarding doesn't work right away. You might get errors about the display, or graphical programs just won't launch. One common issue is that the `DISPLAY` environment variable isn't set correctly on the remote machine. This variable tells graphical programs where to send their output. If it's not set, or set incorrectly, the program won't know where to show its window, which is a bit of a problem.
Another thing to check is that you have an X server running on your local machine. On Linux, this is usually built-in. On Windows, you might need to install a program like VcXsrv or Cygwin/X. Also, firewalls can block X11 traffic, so make sure your firewall isn't getting in the way. It can be a bit finicky sometimes, but once it works, it's pretty reliable, honestly.
Common SSH Challenges and Solutions
Even with the best intentions, you might run into a few bumps when setting up or using SSH. It's pretty normal for tech things to have their quirks. The good news is that many common issues have straightforward solutions, and often, someone else has already figured out a fix. We'll go over a few typical problems you might encounter and how to deal with them, which is helpful.
Understanding these common challenges can save you a lot of time and frustration. It's about knowing what to look for when something isn't quite working as you expect. From connection freezes to issues after installing new software, there are usually logical reasons for what's happening, and pretty simple steps to get things back on track, you know.
Connection Freezes and Timeouts
It can be really annoying when your terminal freezes during an SSH session. This happens to people who SSH from, say, a Fedora machine to an Ubuntu machine, and while it works properly at work, the terminal freezes after a short while. This often comes down to network stability or SSH client/server timeouts. Your connection might be dropping packets, or one side is waiting for a response that never comes, which is frustrating.
To help with this, you can configure your SSH client to send "keep-alive" messages. This tells the server that you are still there, even if you are not actively typing commands. You can add `ServerAliveInterval 60` to your client's `~/.ssh/config` file. This tells your client to send a null packet to the server every 60 seconds if no data has been received from the server, which can often prevent those annoying freezes, so that's a good tip.

Comprehensive Guide To SSH IoT Device Router Setup
Mastering SSH IoT Device Router Setup: A Comprehensive Guide
IoT router|Products and Services|For all your IoT, cloud and AI needs