Control Raspberry Pi Behind Router: Your Guide To Remote Access
Feeling a bit stuck with your Raspberry Pi when you are not at home? It's like having a helpful little computer, but it only really works when you are right there with it, isn't it? Well, you can absolutely take charge of that situation instead of feeling a bit overwhelmed or perhaps powerless. Getting your Raspberry Pi to listen to your commands from anywhere, even if it is tucked away behind your home router, is totally possible. It just takes a few steps, and we are going to walk through them together.
A lot of folks get a Raspberry Pi for all sorts of cool projects, like building a media server, setting up smart home gadgets, or maybe even hosting a personal website. The trouble often comes when you want to check on your project or make changes while you are out and about. Your home router, which is there to keep your network safe, also acts like a bouncer, usually stopping outside connections from reaching your Pi. This can be a real head-scratcher for many.
This guide will show you how to truly `control raspberry pi behind router`. We will look at different ways to get that connection going, talking about what each method involves, what is good about it, and what you might want to watch out for. We will cover everything from direct ways to connect to more secure options, helping you pick the best path for your own needs. You will be able to manage your Pi from anywhere, which is pretty neat.
- When Did Tony Halme Serve In The Finnish Parliament
- Actors On Secret Life Of An American Teenager
- Tim Dillon
- Best Acrylic Powder
- Zefoy Followers
Table of Contents
- The Challenge of Remote Access
- Common Methods to Control Raspberry Pi Behind Router
- Security Best Practices for Remote Pi Access
- Troubleshooting Common Issues
- Frequently Asked Questions
- Final Thoughts on Controlling Your Pi
The Challenge of Remote Access
So, you have your Raspberry Pi humming along nicely inside your home network. You can connect to it easily from your laptop or phone when you are on the same Wi-Fi. But what happens when you are at a coffee shop, or maybe visiting family, and you want to check on your Pi? That is when things get a little trickier, basically.
Why Your Router Is a Barrier
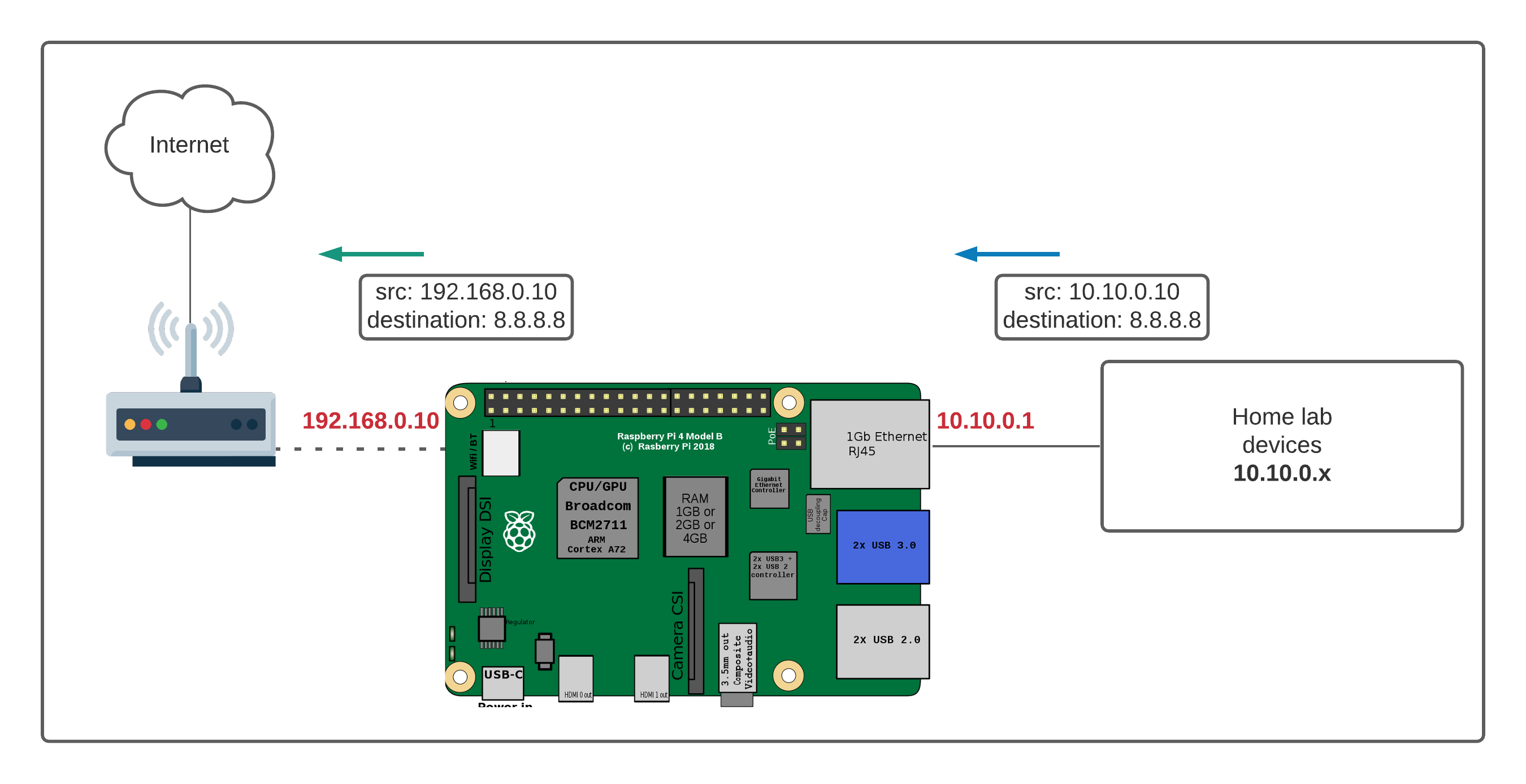
Your home router, you know, that box with all the blinking lights, acts like a security guard for your home network. It lets information go out to the internet, but it is very careful about what comes in. This is a good thing for keeping your devices safe from unwanted visitors. However, it also means that direct connections from the outside world to your Raspberry Pi are usually blocked by default, which is pretty common.
This blocking is part of a security measure called Network Address Translation, or NAT. It lets many devices in your home share one public internet address. When an outside request comes in, the router does not know which of your many devices it is meant for, so it just drops the connection, apparently. This is why you cannot just type in your home IP address and expect to reach your Pi.
- Somali Nudge Linkedin Telegram Link 2022
- Lea County Sheriffs Department
- Tia Kemp Age 47
- Is David Bromstad Married To A Woman
- Joaquin Phoenix Name Change
What You Need to Know First
Before you try to `control raspberry pi behind router`, it helps to understand a few things. You will want to know your Pi's local IP address, which you can find with a simple command like `hostname -I`. Also, you will need to know your router's login details, as you will likely be making some changes there. Knowing your internet service provider's setup can also be helpful, as some providers have certain restrictions, you know.
It is also a good idea to make sure your Raspberry Pi is updated. Running `sudo apt update` and `sudo apt upgrade` will get you the latest software. This helps with both security and making sure everything works smoothly. A fresh system is often a happy system, so to speak.
Common Methods to Control Raspberry Pi Behind Router
There are several ways to get around your router's protective measures and reach your Raspberry Pi. Each method has its own set of steps and different levels of security and convenience. We will go through the most popular options, giving you a clear picture of how each one works, so you can pick what feels right for you.
Method 1: Port Forwarding and Dynamic DNS
This is often the first method people think of when trying to `control raspberry pi behind router`. It involves telling your router to send specific types of incoming traffic directly to your Raspberry Pi. It is like telling the security guard at the gate, "Hey, if someone asks for a specific room number, send them straight to this one."
How Port Forwarding Works
Port forwarding tells your router to take incoming requests on a specific "port" (think of it as a specific door number) and direct them to a specific device on your home network, using that device's local IP address and a different port. For example, you might tell your router that any incoming connection on port 22 (the standard SSH port) should go to your Pi's internal IP address, also on port 22. This makes it possible for you to SSH into your Pi from anywhere, which is rather convenient.
To set this up, you usually log into your router's administration page. You will look for a section labeled "Port Forwarding," "NAT," or "Virtual Servers." Here, you will create a new rule. You will need to specify the external port (what you will connect to from outside), the internal port (what your Pi listens on), the Pi's internal IP address, and the protocol (TCP or UDP). It is pretty straightforward once you find the right settings, you know.
Setting Up Dynamic DNS (DDNS)
Most home internet connections have what is called a "dynamic IP address." This means your public IP address, the one the rest of the internet sees, changes from time to time. If it changes, your port forwarding setup will stop working because the outside world will be looking for your Pi at the wrong address. This is where Dynamic DNS, or DDNS, comes in handy.
A DDNS service gives you a fixed hostname, like `myraspberrypi.ddns.net`, that always points to your home's current public IP address. Your router, or sometimes a piece of software on your Pi, will periodically tell the DDNS service what your current IP address is. This way, you can always use the easy-to-remember hostname to reach your Pi, even if your actual IP address changes, which is quite useful, honestly.
Security Considerations for Port Forwarding
While port forwarding is simple, it does open a direct door to your Raspberry Pi from the internet. This means it can be less secure if not handled carefully. You are basically exposing a service on your Pi directly to the whole internet. This is why it is very, very important to make sure your Pi's security is top-notch. You should absolutely use strong passwords, consider using SSH keys instead of passwords, and keep your Pi's software updated. Limiting access to specific IP addresses if possible can also help, basically.
If you only need SSH access, just forward port 22. Do not forward more ports than you truly need. Every open port is a potential entry point, so less is definitely more when it comes to security. You want to control the situation, not leave it wide open, so to speak.
Method 2: Virtual Private Network (VPN)
Setting up a VPN server on your Raspberry Pi is a much more secure way to `control raspberry pi behind router`. Instead of opening specific doors to your Pi, you create a secure tunnel into your entire home network. Once you are connected to your home VPN, your remote device acts as if it is physically inside your home network, which is pretty cool.
How a VPN Server on Your Pi Works
When you set up a VPN server on your Pi, your remote device (like your laptop or phone) connects to it through an encrypted tunnel. All your internet traffic from that remote device then goes through your home network. This means you can access any device on your home network, including your Pi, using its local IP address, just as if you were sitting at home. It is a very secure way to connect, truly.
This method usually requires port forwarding just one port on your router for the VPN connection itself, rather than forwarding multiple ports for different services. This reduces the number of open doors to your network, making it generally safer. You are still opening a door, but it is a very specific, locked door that only your VPN client knows how to open, you know.
Setting Up OpenVPN or WireGuard
Two popular choices for setting up a VPN server on a Raspberry Pi are OpenVPN and WireGuard. OpenVPN has been around for a long time and is very robust, but it can be a bit more complex to set up. WireGuard is newer, often faster, and simpler to configure, making it a favorite for many Pi users these days. Both are excellent choices for creating a secure tunnel.
There are many guides online for setting up either of these on a Raspberry Pi. You will typically install the server software, generate configuration files, and then import those files into a VPN client on your remote device. It sounds a little involved, but many scripts exist to automate most of the process, making it much easier than it sounds, honestly.
Benefits of Using a VPN
The main benefit of a VPN is security. All your traffic between your remote device and your home network is encrypted. This means snoopers cannot easily see what you are doing. Plus, once connected, you have full access to all your home network devices, not just your Pi. This is great for accessing other smart home devices, network storage, or even other computers, which is very handy. It gives you a lot more control over your entire home network, in a way.
It also means you do not have to expose individual services on your Pi to the internet. If you want to access a web server on your Pi, you just connect to the VPN, and then you can access it via its local IP address, just like you would at home. This keeps those services much safer from direct attacks, basically.
Method 3: SSH Reverse Tunnel
An SSH reverse tunnel is a clever way to `control raspberry pi behind router` without needing to change any settings on your router, like port forwarding. This method is particularly useful if you do not have access to your router's settings, or if your internet service provider uses something called "carrier-grade NAT," which makes port forwarding impossible. It is a bit like your Pi calling out to a friend on the internet and asking that friend to hold open a line for you to call back in.
What Is an SSH Reverse Tunnel?
With a reverse tunnel, your Raspberry Pi makes an outgoing SSH connection to a third-party server (often called a "jump host" or "VPS" – a small, inexpensive virtual private server you rent online). It then tells that server to open a specific port and forward any traffic on that port back through the established SSH connection to your Pi. When you want to connect to your Pi, you simply SSH into that third-party server on the designated port, and your connection is then bounced back to your Pi. It is a neat trick, truly.
The beauty of this is that the initial connection is outbound from your Pi, which routers usually allow without any special configuration. The router sees it as normal outgoing traffic, so it does not block it. This means you bypass the need for port forwarding entirely, which is pretty cool, honestly.
How to Set One Up
You will need a publicly accessible server somewhere on the internet. This could be a cheap VPS from a provider like DigitalOcean or Linode. On your Raspberry Pi, you would run a command similar to `ssh -R 8080:localhost:22 user@your_vps_ip`. This tells your Pi to create a tunnel where traffic to port 8080 on your VPS is sent back to port 22 (SSH) on your Pi. Then, from your remote computer, you would connect to your Pi by doing `ssh -p 8080 user@your_vps_ip`. It is a two-step process, but very effective.
For persistent connections, you might use a tool like `autossh` on your Pi. This tool keeps the tunnel alive even if the connection drops, which is very helpful. Setting this up as a system service means it will start automatically when your Pi boots up, making it quite reliable, you know.
When to Use This Method
This method is great when other options are not available. If you are on a network where you cannot change router settings, or if your ISP's setup prevents direct incoming connections, an SSH reverse tunnel is a fantastic workaround. It offers good security because the tunnel itself is encrypted, and you are not directly exposing your Pi's services to the internet. It is a bit more involved to set up than simple port forwarding, but the flexibility it offers is a big plus, apparently.
It is also a good choice if you only need to access your Pi occasionally or for specific tasks, as it provides a direct, secure path. However, it does rely on that third-party server being available and reliable, so pick a good one, basically.
Method 4: Cloud-Based Services
Another way to `control raspberry pi behind router` without router changes is to use cloud-based services. These services act as a middleman, allowing your Pi to connect to them and then allowing you to connect to the service to reach your Pi. This can be very user-friendly, especially for those who are not comfortable with network configurations.
Using Ngrok or Similar Tools
Ngrok is a popular example of such a service. Your Raspberry Pi runs a small client application that establishes an outbound connection to the Ngrok cloud. Ngrok then gives you a public URL that tunnels incoming requests directly to your Pi. For example, if you are running a web server on your Pi, Ngrok can provide a public `https://your-random-id.ngrok.io` address that connects directly to your Pi's web server. It is pretty simple to get going, really.
Other similar services exist, some specifically for IoT devices or remote access. They typically involve installing a small agent on your Pi, which then registers with the cloud service. You then use the service's website or app to connect to your Pi. This takes away a lot of the headache of network setup, which is nice, honestly.
Other Cloud Platforms
Beyond simple tunneling services, you could also use platforms like TeamViewer, AnyDesk, or even some specialized Raspberry Pi remote access services. These often provide a graphical interface for controlling your Pi, making it feel just like you are sitting in front of it. They handle all the network magic in the background, which is quite convenient, you know.
Some platforms are designed specifically for managing fleets of IoT devices, which could include many Raspberry Pis. These might offer features like remote command execution, monitoring, and even over-the-air updates. They are usually more for larger projects, but some have free tiers for personal use, apparently.
Ease of Use Versus Privacy
The biggest advantage of cloud-based services is how easy they are to set up and use. You often do not need to touch your router settings at all. However, you are relying on a third-party service to relay your connections. This means your data is passing through their servers, so you need to trust that service with your privacy and security. Always read their terms of service and privacy policy carefully. For simple projects or quick access, they are great, but for very sensitive data, you might prefer a self-hosted VPN, basically.
It is a trade-off between convenience and having complete control over your data's path. For many people, the ease of use makes these services a very attractive option for controlling their Pi from afar, which is fair enough.
Security Best Practices for Remote Pi Access
No matter which method you choose to `control raspberry pi behind router`, security should always be a top priority. Opening your Pi to the internet, even through a tunnel, means you are increasing its exposure. Taking a few simple steps can make a big difference in keeping your Pi safe from unwanted access, you know.
- Change Default Passwords: This is absolutely crucial. The default username `pi` with password `raspberry` is widely known. Change it immediately. Use a strong, unique password for your `pi` user, or even better, create a new user and disable the `pi` user.
- Use SSH Keys: For SSH access, switch from password authentication to SSH keys. This is much more secure. It involves generating a pair of cryptographic keys, keeping one private on your computer and placing the public one on your Pi. No password can be guessed, which is very, very good.
- Keep Software Updated: Regularly run `sudo apt update` and `sudo apt upgrade` on your Raspberry Pi. Software updates often include security fixes that patch vulnerabilities. An outdated system is an open invitation for problems, apparently.
- Firewall Your Pi: Even if your router has a firewall, setting up a firewall on your Pi itself (like `ufw`) adds an extra layer of protection. You can configure it to only allow connections on specific ports from specific IP addresses, if you know them. This is a very good habit to get into.
- Disable Unused Services: If you are not using a particular service on your Pi, disable it. Every running service is a potential point of weakness. Less running means less to worry about, which is simple logic, truly.
- Monitor Logs: Periodically check your Pi's system logs for unusual activity. Logs can tell you if someone is trying to access your Pi without permission. This is a bit like keeping an eye on who is knocking at your digital door.
By following these practices, you can significantly reduce the risk of your Raspberry Pi being compromised. Taking `control` also means taking control of its safety, you see.
Troubleshooting Common Issues
Sometimes, getting things to work just right can be a bit of a puzzle. If you are having trouble connecting to `control raspberry pi behind router`, here are some common things to check. It is almost always something small that just needs a little adjustment, basically.
- Double-Check IP Addresses: Make sure you have the correct public IP address for your home (if using port forwarding) or the correct local IP address for your Pi. Sometimes, a router restart can change your Pi's local IP if it is not set to static.
- Verify Port Forwarding Rules: If you are using port forwarding, log into your router and make sure the rules are exactly right. Check the external port, internal port, internal IP address, and protocol (TCP/UDP). A single typo can stop everything from working, you know.
- Firewall on Pi: Did you set up a firewall on your Pi? It might be blocking your incoming connections. Try temporarily disabling it (e.g., `sudo ufw disable`) to see if that is the issue. If it works, then you need to add a rule to allow your connection.
- ISP Restrictions: Some internet service providers block certain ports or use Carrier-Grade NAT (CGNAT), which prevents direct incoming connections. If you suspect this, contact your ISP or consider methods like SSH reverse tunnels or cloud services.
- DDNS Not Updating: If using DDNS, check if your DDNS client (on your router or Pi) is correctly updating your public IP address with the DDNS service. You can often check your current public IP on websites like `whatismyip.com` and compare it to what your DDNS service thinks it is.
- Restart Everything: Sometimes, a simple restart of your Raspberry Pi, your router, and your remote device can clear up temporary glitches. It is like giving everything a fresh start, which often helps, honestly.
Troubleshooting is part of the learning process. Do not get discouraged if it does not work on the first try. A little patience and systematic checking usually lead to a solution, you know.
Frequently Asked Questions
Here are some common questions people often ask when trying to `control raspberry pi behind router`.
How do I access my Raspberry Pi from outside my home network?
You can access your Raspberry Pi from outside your home network using several methods. These include setting up port forwarding on your router, creating a VPN server on your Pi, using an SSH reverse tunnel to a public server, or employing cloud-based remote access services like Ngrok. Each method offers a different balance of complexity, security, and convenience, so you can pick what suits your setup, basically.
Is it safe to port forward for my Raspberry Pi?
Port forwarding can be safe if done with strong security practices. You should always use robust passwords, consider SSH key authentication, keep your Pi's software fully updated, and only forward the specific ports you absolutely need. Limiting access to known IP addresses with a firewall on your Pi adds another layer of protection. Without these precautions, port forwarding can expose your Pi to risks, you know.
Can I control my Raspberry Pi without port forwarding?
Yes, you can definitely `control raspberry pi behind router` without port forwarding. Methods like setting up a VPN server on your Pi (which typically only requires forwarding one VPN port, not individual service ports), using an SSH reverse tunnel to a third-party server, or utilizing cloud-based remote access services like Ngrok allow you to bypass direct port forwarding while still gaining remote access. These options are often preferred for their enhanced security or ability to work around ISP restrictions, which is pretty neat.
Final Thoughts on Controlling Your Pi
Getting your Raspberry Pi to `control raspberry pi behind router` truly puts the power in your hands. Whether you are checking on a smart home project while on vacation, or just need to grab a file from your personal server, knowing how to connect remotely makes your Pi much more useful. It allows you to take charge of your setup, rather than feeling limited by your home network's boundaries. The key is to pick the method that fits your comfort level with technical setup and your security needs, you know.
Remember that the internet is a vast place, and keeping your devices secure is always important. A little care in setting up strong passwords, using SSH keys, and keeping your software current goes a very, very long way. So, go ahead, experiment with these methods, and enjoy the freedom of having your Raspberry Pi accessible from anywhere. You can always learn more about Raspberry Pi projects on our site, and if you are looking for advanced tips, check out our guide to network security for more information, which is helpful.
- Is Raven A Demon
- Bill Jordan Net Worth
- How Old Is Paul Hollywood
- Tori Black Current Activities
- Princess Amelia Wu Princessameliaofficial Latest
Someone made a Raspberry Pi router you can control with your smartphone
Control Raspberry Pi Behind Router Windows 10 Free: A Comprehensive Guide
Control Raspberry Pi Behind Router IoT Free Android: A Comprehensive Guide