Gain Remote Control Of Your Raspberry Pi Behind Router NAT
Ever feel like your awesome Raspberry Pi project is stuck behind a digital wall, unreachable when you are away from home? It is a common frustration, really. You set up a cool home automation system, a little media server, or maybe a tiny web server on your Pi, and then you realize you cannot get to it from work or while traveling. This happens because of something called Network Address Translation, or NAT, which your home router uses. It is a bit like having a house with many rooms but only one main door to the outside world. You want to take control of the situation, rather than feeling powerless, to make your Pi accessible whenever you need it.
Many folks use their Raspberry Pis for all sorts of neat things, from monitoring plants to running personal cloud storage. The idea of checking on your setup, or perhaps tweaking a setting, from anywhere is super appealing. Yet, that router, while keeping your home network safe, also keeps your Pi hidden from the wider internet. So, how do you bridge that gap?
This guide will walk you through several good ways to make your Raspberry Pi reachable from anywhere, even when it is tucked away behind your router's NAT. We will look at different approaches, discussing how each one works and what might be a good fit for you, so you can essentially gain remote access to your little computer.
- Joe Pesci Ok Ok Ok
- Sydney Mclaughlin Levrone Parents
- Redbox Founder
- Can Ka Vip Telegram
- Is Morgan Wallen Dating Anyone
Table of Contents
- What is NAT and Why It is a Challenge?
- Common Methods for Remote Pi Access
- Choosing the Right Method for You
- Security Best Practices for Remote Access
- Frequently Asked Questions
What is NAT and Why It is a Challenge?
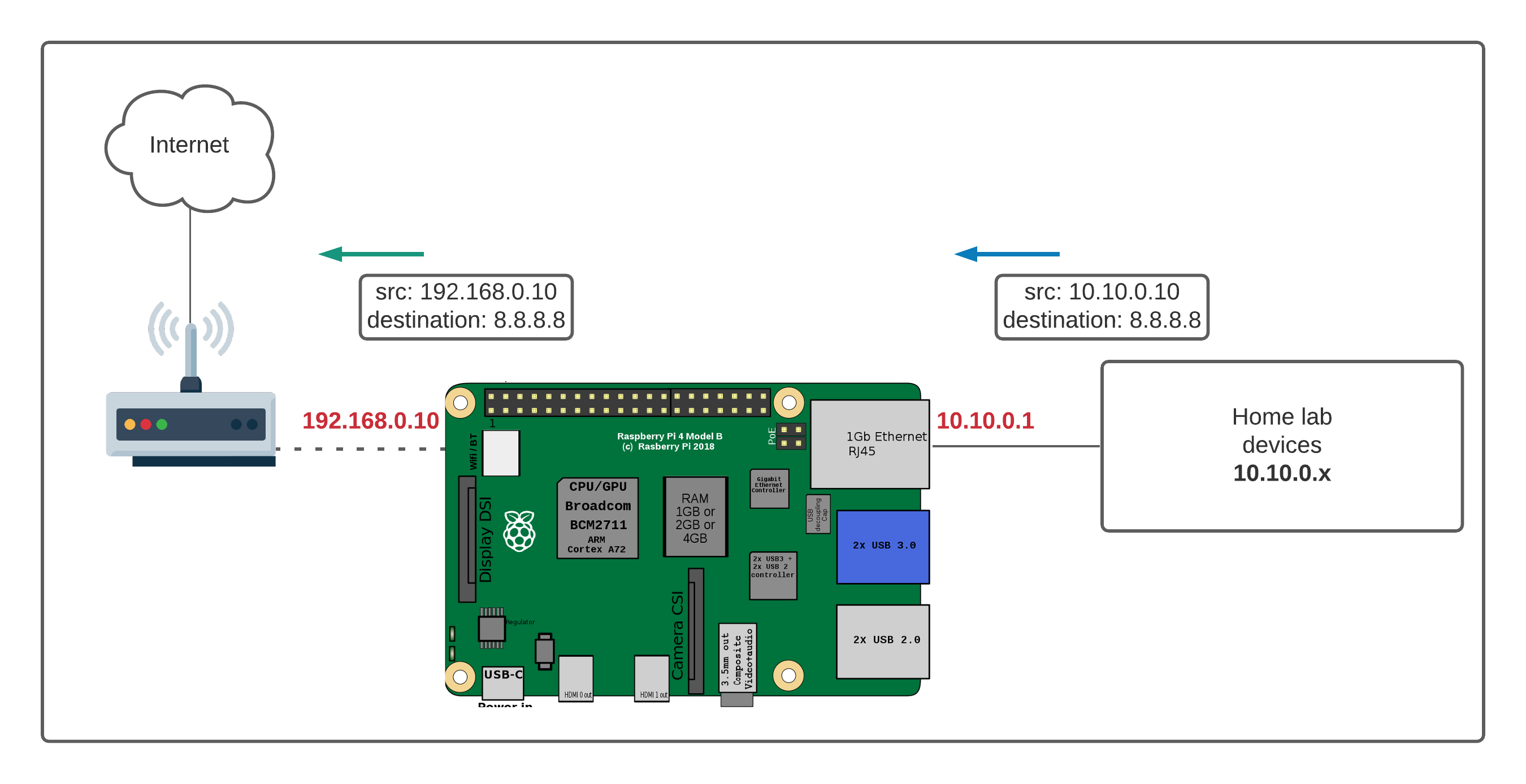
So, what exactly is NAT? Well, it is a network process your router uses. Think of it like this: your internet service provider, or ISP, gives your home one public internet address. That one address is how the rest of the internet sees your entire home network. Inside your home, though, your router gives each of your devices, like your phone, laptop, and Raspberry Pi, its own private address. These private addresses are only known within your home network.
When your Raspberry Pi wants to send information out to the internet, the router changes the Pi's private address to your home's single public address. When information comes back, the router knows which internal device it should send that information to. This is generally good for security, as outside devices cannot easily "see" your Pi's private address directly. However, it also means that if you try to connect to your Pi from outside your home, the router does not automatically know which internal device you want to reach. It is a bit like trying to call a specific person in a large office building by only knowing the building's main phone number, without an extension.
This setup, while useful for sharing one public IP address among many devices and adding a layer of protection, creates a bit of a hurdle for remote access. You cannot simply type in your home's public IP address and expect to connect to your Pi directly. That is where the challenge comes in for those who want to control raspberry pi behind router nat.
Common Methods for Remote Pi Access
There are several good ways to get around the NAT hurdle and gain remote access to your Raspberry Pi. Each way has its own steps and things to think about, so you can pick what fits your needs best. We will look at some of the most popular and reliable methods, so you can, you know, really take charge of your Pi.
Port Forwarding: The Traditional Way
Port forwarding is, in a way, the most traditional method for allowing outside connections to a device on your home network. It tells your router, "Hey, if someone tries to connect to this specific port on my public internet address, send that connection straight to my Raspberry Pi on its private address and a specific port." It is like setting up a specific extension number for your Pi in that office building example.
To set this up, you usually need to log into your router's settings, which you can typically do through a web browser. You will find a section for "Port Forwarding" or "NAT Forwarding." There, you will specify:
- The external port you want to use (e.g., 2222 for SSH).
- The internal IP address of your Raspberry Pi (e.g., 192.168.1.100).
- The internal port on your Raspberry Pi that the service is running on (e.g., 22 for SSH, 80 for a web server).
It is usually a good idea to give your Raspberry Pi a static IP address on your local network. This way, its internal address does not change, and your port forwarding rule always points to the correct device. Otherwise, your Pi might get a different internal address from the router, and your remote connection would just stop working, which is annoying.
The good points of port forwarding are that it is generally simple to set up if you are comfortable with router settings, and it offers direct access. However, there are some downsides. It can be a bit less secure, as it opens a specific "door" directly to your Pi from the internet. You also need to have a static public IP address from your ISP, or use a dynamic DNS service, because your home's public IP might change sometimes. Dynamic DNS, or DDNS, services help by giving you a consistent hostname that always points to your changing public IP.
Reverse SSH Tunneling: A Clever Workaround
Reverse SSH tunneling is, arguably, a very clever way to get around NAT without needing to mess with your router's port forwarding settings. This method involves your Raspberry Pi initiating a connection outwards to a publicly accessible server, and then keeping that connection open. This creates a "tunnel" through which you can then connect back to your Pi. It is like your Pi calling you from inside the house and saying, "Here, you can talk to me through this line!"
For this to work, you will need a third-party server that has a public IP address and is always online. This could be a cheap virtual private server, or VPS, that you rent, or even another computer you own that is always connected to the internet with a public IP. Your Raspberry Pi connects to this intermediate server via SSH, creating the tunnel.
Here is how it generally works:
- Your Raspberry Pi connects to the public server.
- It tells the public server to open a specific port.
- Any connection made to that specific port on the public server is then sent back through the tunnel to your Raspberry Pi.
This method is quite secure because the connection is initiated by the Pi, and it does not require opening any incoming ports on your home router. It is also really good if your ISP uses something called "Carrier-Grade NAT," or CGNAT, which makes traditional port forwarding impossible. The main challenge is setting up and maintaining that intermediate server, which might cost a little money or require some technical know-how. You also need to make sure the SSH connection from your Pi to the server stays alive, perhaps using a tool like `autossh`.
VPN Solutions: Secure and Private Access
Using a Virtual Private Network, or VPN, is another very secure and flexible way to control raspberry pi behind router nat. With a VPN, you essentially create a private, encrypted connection between your remote device and your home network. It is like building a secret, protected pathway directly into your house. Once connected to the VPN, your remote device acts as if it is physically on your home network, so you can access your Pi just as if you were sitting right next to it.
There are two main ways to use a VPN for this purpose:
Run a VPN server on your Raspberry Pi: You can set up your Pi itself to act as a VPN server using software like OpenVPN or WireGuard. This is a very common approach. When you are away, you connect your laptop or phone to your Pi's VPN server. This creates a secure tunnel, and suddenly your remote device can see all the devices on your home network, including your Pi. This method usually still requires port forwarding for the VPN server's port on your router, or you can combine it with a reverse SSH tunnel to get around that.
Setting up a VPN server on your Pi can be a bit more involved, but there are many good guides out there. It gives you a lot of control and a very secure connection.
Use a commercial VPN service: Some commercial VPN providers offer a feature where you can get a dedicated IP address, or they might allow you to forward ports through their service. This is less common for directly accessing devices *within* your home network, but it can be an option if your Pi is connected to the VPN service itself and you want to reach it through that service's IP. This is generally more about protecting your Pi's outgoing traffic than providing incoming remote access, unless the provider specifically offers a way to reach devices behind their VPN.
VPNs are fantastic for security and privacy, as all your traffic is encrypted. They can be a bit more complex to set up initially, especially if you are hosting the server yourself. However, once it is working, it provides a very robust way to access not just your Pi, but potentially other devices on your home network too.
Cloud Services & IoT Platforms: The Easy Route
For those who prefer a simpler, less hands-on approach, various cloud services and IoT platforms offer ways to control raspberry pi behind router nat. These services typically involve installing a small piece of software, an agent, on your Raspberry Pi. This agent then connects to the service's cloud infrastructure, creating a pathway that bypasses NAT. It is like giving your Pi a special direct line to a global switchboard, which then connects you.
Some popular examples include:
ngrok: This service creates a secure tunnel from a public URL to a local port on your Raspberry Pi. It is really good for quickly exposing a web server or other local service to the internet for testing or temporary access. You just run a command on your Pi, and ngrok gives you a public URL. This is super handy for showing off a project without much fuss.
It is generally very simple to set up, but the free tier often gives you a random URL that changes each time, which is not ideal for permanent access. Paid plans offer static URLs and more features.
Dataplicity: This service is made specifically for Raspberry Pi remote access. You install a single command on your Pi, and it connects to Dataplicity's cloud. You then get a web-based terminal to access your Pi, and you can even set up "wormholes" to expose specific services like a web server or camera feed. It is incredibly user-friendly and great for basic remote control and monitoring.
Dataplicity is known for being very easy to use, and it does not require any router changes. The free tier has some limitations, but it is a good starting point for many.
Remote.it: This service also creates secure connections to your devices behind NAT. You install an agent on your Pi, register your device, and then you can access various services (SSH, VNC, HTTP, etc.) through their platform. It is a bit more versatile than Dataplicity, offering connections to many different types of services.
Remote.it is pretty robust and offers a good balance of ease of use and flexibility. Like other cloud services, it relies on their infrastructure, so you are dependent on them for uptime and features.
These cloud-based services are often the easiest to get going, especially if you are not comfortable with network settings. They handle the NAT traversal for you. The main considerations are trusting the third-party service with your connections and potential costs for advanced features or sustained use.
Choosing the Right Method for You
Deciding which way to control raspberry pi behind router nat is best for you really depends on a few things. You might want to think about how comfortable you are with technical setup, what kind of security you need, and whether you are willing to pay for a service.
For quick, temporary access or testing a web service: ngrok is usually a good choice. It is fast to set up and very effective for short bursts of access.
For basic, user-friendly remote control and monitoring: Dataplicity is often a great pick. It is simple to get started and provides a good web interface.
For general-purpose, secure access to various services without router changes: Remote.it or a reverse SSH tunnel are strong contenders. Remote.it is easier, while reverse SSH gives you more control if you have a public server.
For the most secure and comprehensive access to your entire home network: Running your own VPN server on the Pi is often the top option. It requires more setup but gives you a lot of power and protection.
For a straightforward, direct connection if you are comfortable with router settings: Port forwarding can work, but remember the security implications and the need for a static IP or DDNS.
Consider your comfort level with command lines versus graphical interfaces, and how much you value privacy versus convenience. Each method has its own sweet spot, so to speak, so you can, like, really get a handle on things.
Security Best Practices for Remote Access
No matter which method you pick to control raspberry pi behind router nat, keeping your Pi and home network safe is extremely important. Opening up your Pi to the internet, even in a small way, means you need to be extra careful. Here are some key things to do to keep things secure:
Change default passwords: This is, honestly, the very first thing you should do. The default username `pi` and password `raspberry` are widely known. Change them immediately to something long and unique.
Use strong, unique passwords: For any accounts related to your Pi, your router, or any cloud services you use, make sure your passwords are complex. Use a mix of upper and lower case letters, numbers, and symbols. A password manager can help you keep track of these.
Use SSH key-based authentication: If you are using SSH (which is common for remote Pi access), switch from password authentication to SSH keys. This is much more secure. It means you use a special pair of cryptographic keys, one on your remote computer and one on your Pi, to prove who you are. This way, even if someone guesses your password, they cannot get in without your private key.
Disable root login via SSH: The `root` user has complete control over your Pi. It is much safer to log in as a regular user and then use `sudo` when you need administrative privileges.
Keep your software updated: Regularly update your Raspberry Pi's operating system and any installed software. This helps patch security holes that attackers might try to use. You can do this with `sudo apt update && sudo apt upgrade`.
Use a firewall: Configure a firewall on your Raspberry Pi, such as `ufw` (Uncomplicated Firewall). This lets you control which incoming and outgoing connections are allowed. For instance, you might only allow SSH connections from specific IP addresses.
Consider two-factor authentication (2FA): If a cloud service you use offers 2FA, turn it on. This adds an extra layer of security, usually requiring a code from your phone in addition to your password.
Monitor logs: Occasionally check your Pi's system logs for any unusual activity. This can help you spot unauthorized access attempts.
Limit exposed services: Only expose the services you absolutely need to the internet. If you only need SSH, do not also expose a web server unless it is necessary. Less open doors mean less risk.
By following these steps, you can greatly reduce the risk of someone getting into your Pi without permission. Taking these precautions is, in fact, a very important part of taking control of your Pi's security.
Frequently Asked Questions
How do I access my Raspberry Pi remotely without port forwarding?
You can access your Raspberry Pi remotely without port forwarding by using methods that involve an outbound connection from your Pi. These include setting up a reverse SSH tunnel to a public server, or using cloud services like Dataplicity, ngrok, or Remote.it. These services help create a connection back to your Pi without you needing to open specific ports on your home router.
Can I use a VPN to access my Raspberry Pi?
Yes, you can definitely use a VPN to access your Raspberry Pi. The most common way is to set up your Raspberry Pi itself as a VPN server (using software like OpenVPN or WireGuard). Then, when you are away, you connect your remote device to that VPN server. Once connected, your remote device will act as if it is on your home network, allowing you to access your Pi and other local devices securely.
What is NAT and why does it block remote access?
NAT, or Network Address Translation, is a process your router uses to let multiple devices on your home network share one public internet address. It translates private internal IP addresses to your single public IP when traffic goes out, and directs incoming traffic back to the right internal device. It blocks remote access because when an external connection tries to come in, the router does not automatically know which internal device (like your Pi) that connection is meant for, unless you specifically tell it through a rule like port forwarding.
To learn more about Raspberry Pi projects on our site, and link to this page here.
For more technical details on networking concepts, you might want to check out resources like the Internet Engineering Task Force (IETF) website, which provides specifications and information on network protocols.
- Famous Ellas
- Gal Gadot Daughters
- Jim Carrey First Film
- Georganne Lapiere Wikipedia
- Ssh Iot Device Router

How to Turn a Raspberry Pi Into a VPN-Secured Travel Router
Someone made a Raspberry Pi router you can control with your smartphone
Control Raspberry Pi Behind Router Windows 10 Free: A Comprehensive Guide