How To Control Raspberry Pi Behind Router IoT Using Clever Methods
Have you ever set up a Raspberry Pi for an internet of things project, only to realize you can't reach it once you're away from home? It's a pretty common situation, isn't it? You might feel a bit stuck, like your little computer is trapped behind a digital wall. This feeling of wanting to manage something remotely, yet finding it just out of reach, is a lot like trying to open a control panel that keeps hiding. We want to be able to make changes, adjust settings, and really take charge of our devices, no matter where we are.
It turns out, your Raspberry Pi sitting on your home network is often shielded by your router. This device, doing its job, basically keeps outside traffic from getting directly to your internal gadgets. So, while it’s great for security, it makes remote access a bit of a puzzle. You can’t just type in an address and expect to connect, you know? It’s almost like your Pi is in its own little world, safe and sound, but also a little isolated.
But don't worry, there are some really smart ways to get around this. We're going to explore how you can get proper access and truly control Raspberry Pi behind router IoT using a few different strategies. These methods will help you stay connected to your projects, whether you're just down the street or on the other side of the planet. So, let's figure out how to bridge that gap and get your Pi working for you, remotely.
- Vanessa Kirby Birth Date
- Luka Age
- Emma Watson Relationship Status
- Richard Ramirez Case Photos
- Keisha Knight Pulliam Net Worth
Table of Contents
- The Challenge of Remote Pi Access
- Method 1: Port Forwarding – A Direct Route
- Method 2: Virtual Private Networks (VPNs) – A Secure Tunnel
- Method 3: Cloud-Based Tunneling Services – Easy Access
- Method 4: Reverse SSH Tunneling – For the Tech-Savvy
- Keeping Your Pi Safe: Security Tips
- Choosing the Best Method for You
- Frequently Asked Questions
The Challenge of Remote Pi Access
So, you’ve got your Raspberry Pi doing its thing, maybe collecting sensor data or running a tiny web server for your smart home. It's working perfectly when you're connected to your home Wi-Fi, isn't it? But then you leave, and suddenly, poof! Your Pi seems to disappear from the internet. This happens because your home router uses something called Network Address Translation, or NAT. It basically acts as a gatekeeper, giving all your devices inside your home a private address that isn't visible from the outside world.
Your router has one public IP address, which is like your home's unique postal address on the internet. All the devices inside, like your phone, laptop, and your Raspberry Pi, share this one public address. When something from the internet tries to reach a device inside your home, the router doesn't really know which specific device it's for, you see? It's a bit like having one mailbox for an entire apartment building; mail comes to the building, but how does it know which apartment to go to?
This setup is actually a good thing for security, as it shields your internal network from direct attacks. However, it does make it tricky if you specifically want to reach your Raspberry Pi from outside. You need a way to tell your router, "Hey, this incoming connection is for my Pi, send it there!" And that, frankly, is where the fun begins.
- Ben Chichoski
- Rinck Herbert
- Elvis Presley Cause Of Death
- Is There A Country Named Lebron
- Chris Brown Concert Typical Set Length
Method 1: Port Forwarding – A Direct Route
What is Port Forwarding?
Port forwarding is, in a way, like telling your router to open a specific door for a specific purpose. Imagine your router as a big office building, and each "port" is a numbered door. When an outside request comes to a certain door number (a port), you tell the router, "If someone knocks on door 22, send them directly to the office of my Raspberry Pi." This allows external connections to reach a specific device and service on your internal network. It's a pretty straightforward way to get things done, you know?
This method is often the first thing people think of when they want to control Raspberry Pi behind router IoT using a direct connection. It works by creating a direct path from a specific port on your public IP address to a specific port on your Raspberry Pi's private IP address. So, if you want to SSH into your Pi, you'd forward port 22 (the standard SSH port) from your router to port 22 on your Pi. It's quite neat, honestly.
Steps to Set Up Port Forwarding
Setting this up usually involves a few steps. First, you'll want to give your Raspberry Pi a static IP address on your local network. This means its internal address won't change, which is important because if it did, your port forwarding rule would break. You can usually do this in your router's settings or by configuring your Pi's network settings directly. It's like giving your Pi a permanent office number in that building.
Next, you need to log into your router's administration panel. This is usually done by typing your router's IP address (often something like 192.168.1.1 or 192.168.0.1) into a web browser. Once you're in, you'll look for a section labeled "Port Forwarding," "NAT," or "Virtual Servers." The exact name can vary a bit depending on your router's brand and model, but it's usually pretty easy to find, you know?
Inside that section, you'll create a new rule. You'll specify the external port (what port people from the outside will connect to), the internal port (what port the service on your Pi is listening on, like 22 for SSH), and the internal IP address of your Raspberry Pi. You might also choose the protocol, usually TCP or UDP, or both. For SSH, it's TCP. Save the settings, and your router should now be ready to direct traffic to your Pi. It’s a bit like setting up a special delivery route.
Things to Think About with Port Forwarding
While port forwarding is effective, it does open a direct path to your Raspberry Pi from the internet. This means you need to be very careful about security. Any service you expose to the internet through port forwarding becomes a potential target for unwanted visitors. So, it's really important to make sure your Pi is secure.
Always use strong, unique passwords, and consider setting up SSH key-based authentication instead of just passwords for SSH access. Keep your Raspberry Pi's operating system and any software on it updated regularly. These updates often include important security fixes. You might also want to set up a firewall on your Pi itself, just to add another layer of protection. It's a bit like putting extra locks on that office door, you know?
Method 2: Virtual Private Networks (VPNs) – A Secure Tunnel
How a VPN Helps
If the idea of directly exposing your Pi makes you a little uneasy, a Virtual Private Network, or VPN, is a fantastic alternative. A VPN creates a secure, encrypted tunnel between your device (like your laptop or phone) and your home network. Once you're connected to your home VPN, it's almost as if your device is physically sitting right there on your home network, even if you're miles away. This allows you to control Raspberry Pi behind router IoT using its local IP address, just like you would if you were at home.
This method means you don't have to open any specific ports on your router for each service on your Pi. Instead, you open just one port for the VPN server itself. All your traffic then goes through that single, secure tunnel. It's a much more private and, frankly, safer way to access your home network and all the devices on it, including your Pi. You get to manage everything as if you were right there, which is pretty cool.
Setting Up a VPN on Your Pi
You can turn your Raspberry Pi into a VPN server itself. Popular choices for this include OpenVPN and WireGuard. OpenVPN is a very established and flexible option, while WireGuard is newer, simpler, and often much faster. Setting either of these up involves installing the software on your Pi and then configuring it to act as a server. There are many good guides available online that walk you through the process step-by-step.
Once your Pi is running as a VPN server, you'll typically need to configure your router to forward one single port to your Pi for the VPN connection. This is usually a UDP port for OpenVPN or WireGuard. Then, on your client device (your laptop, phone, etc.), you'll install the corresponding VPN client software and import the configuration file generated by your Pi. Once connected, you'll be able to access your Pi and other devices on your home network as if you were local. It’s honestly a very clean solution.
Advantages and Disadvantages of VPNs
The main advantage of using a VPN is the security it offers. All your traffic is encrypted, and you're not exposing multiple services directly to the internet. It also gives you access to your entire home network, not just your Pi. This means you could, say, access other network drives or smart home hubs. It's a comprehensive solution, you know?
On the flip side, setting up a VPN server can be a bit more involved than simple port forwarding. You need to understand a little about networking and server configuration. Also, your home internet connection's upload speed will affect the performance of your VPN. If your upload speed is slow, your remote connection might feel a bit sluggish. Nevertheless, for many, the added security and flexibility are well worth the extra effort.
Method 3: Cloud-Based Tunneling Services – Easy Access
How These Services Work
If you're looking for a simpler approach that bypasses router configuration entirely, cloud-based tunneling services are a fantastic option. These services create an outbound connection from your Raspberry Pi to their cloud servers. Your Pi initiates the connection, which means your router sees it as normal outgoing traffic, so no special port forwarding is needed on your router. Then, when you want to connect to your Pi, you connect to the service's cloud server, and it forwards your request through the established tunnel to your Pi.
This method is particularly good if you have a router that's difficult to configure, or if your internet service provider (ISP) uses something called Carrier-Grade NAT (CGNAT), which makes traditional port forwarding impossible. It's a very user-friendly way to control Raspberry Pi behind router IoT using a managed solution. You essentially rely on a third-party service to act as the middleman, making the connection process much smoother.
Popular Options and Their Use
Several services offer this kind of tunneling. Ngrok is a very popular one for temporarily exposing local web servers or SSH connections. You install a small client on your Pi, tell it which local port to expose (like 22 for SSH or 80 for a web server), and it gives you a public URL you can use to connect. It's incredibly quick to set up for testing purposes, honestly.
Other services like Remote.it and Dataplicity are designed more specifically for long-term remote access to IoT devices. They typically involve installing a daemon or agent on your Raspberry Pi. Once installed and configured, your Pi registers with their service, and you can then access your Pi's services (like SSH, VNC, or web interfaces) through their web portal or dedicated client applications. They often provide a dashboard to manage multiple devices, which is quite handy.
Benefits and Drawbacks of Cloud Tunnels
The biggest benefit here is the ease of setup and the ability to bypass tricky router configurations or CGNAT. You don't need to mess with your router's settings at all, which is a huge plus for many people. These services often provide a stable connection, and some even offer features like secure logging and device management. It's a very convenient way to get things done, you know?
However, the main drawback is that you are relying on a third-party service. This means your data is passing through their servers, and you're dependent on their uptime and security practices. While reputable services are generally trustworthy, it's something to consider for very sensitive applications. Also, free tiers often have limitations on bandwidth or connection time, so you might need to pay for a subscription for continuous, heavy use. But for many hobby projects, the free tiers are often sufficient.
Method 4: Reverse SSH Tunneling – For the Tech-Savvy
What is Reverse SSH?
Reverse SSH tunneling is a clever, more advanced technique that also helps you control Raspberry Pi behind router IoT using an outbound connection, much like the cloud services, but without relying on a third-party platform. It involves your Raspberry Pi initiating an SSH connection to a publicly accessible server (which you control, or rent cheaply). This connection creates a "tunnel" back to your Pi.
Once this tunnel is established, you can then connect to your publicly accessible server, and from there, access your Raspberry Pi through the tunnel. It's a bit like your Pi calling a friend's phone (the public server) and leaving a line open, so you can call the friend's phone and get connected directly to your Pi through that open line. It's a very direct and secure way to do things, if you know how.
When to Use It
This method is great if you want complete control and don't want to rely on a third-party service for continuous access. You'll need a public server with a static IP address, which you can usually get very cheaply from a cloud provider. Your Pi will need to establish a persistent SSH connection to this server, often using SSH keys for security and automation.
It requires a bit more technical know-how to set up and maintain, as you're managing both the Pi and the public server. You'll need to ensure the SSH connection stays alive, perhaps using a tool like `autossh`. However, for those who are comfortable with command-line interfaces and want a robust, self-managed solution, it's a very powerful technique. It gives you a lot of freedom, honestly.
Keeping Your Pi Safe: Security Tips
No matter which method you choose to control Raspberry Pi behind router IoT using, security should always be a top concern. When you open your Pi to the outside world, even through a tunnel, you're creating a potential entry point. So, taking some basic precautions is really important.
First off, change the default password for the 'pi' user immediately, or even better, create a new user and disable the 'pi' user. Use strong, unique passwords for any accounts on your Pi. For SSH access, switch from password authentication to SSH key-based authentication. This is much more secure, as it relies on cryptographic keys rather than something that can be guessed or brute-forced.
Keep your Raspberry Pi's operating system (Raspberry Pi OS) and all installed software up to date. Regular updates often include security patches that fix known vulnerabilities. You can do this with `sudo apt update` and `sudo apt upgrade`. Also, consider setting up a basic firewall on your Pi using `ufw` (Uncomplicated Firewall) to only allow connections on the ports you absolutely need. It's a bit like having a security guard for your Pi, you know?
If you're using port forwarding, try to use a non-standard external port. For example, instead of forwarding external port 22 to internal port 22 for SSH, you could forward external port 2222 to internal port 22. This won't stop a determined attacker, but it does deter automated scanning bots that only check standard ports. It's a small step that can make a difference.
Choosing the Best Method for You
So, with all these options, how do you pick the right one to control Raspberry Pi behind router IoT using? It really depends on your comfort level with technical setups, your specific needs, and how much security you want.
If you're just starting out and want something quick and relatively simple for occasional access or testing, a cloud-based tunneling service like Ngrok or Dataplicity might be a good fit. They handle a lot of the network complexities for you, which is pretty convenient.
For a more secure and comprehensive solution, especially if you want access to your entire home network, setting up a VPN server on your Pi is an excellent choice. It gives you a lot of control and peace of mind, though it does require a bit more initial setup. Learn more about network security on our site, you know?
Port forwarding is a direct and simple approach for specific services, but it demands careful attention to security on your Pi itself. If you're confident in securing your Pi and only need to expose one or two services, it can work well.
Finally, reverse SSH tunneling is for those who are comfortable with Linux command lines and want a self-managed, highly customizable solution without relying on third parties. It's a very powerful tool for advanced users, honestly. Whatever you choose, remember that the goal is to keep your Pi working for you, wherever you are. We've found that having this kind of control over your devices makes all the difference in your IoT projects.
Frequently Asked Questions
Q1: Is it safe to port forward my Raspberry Pi?
It can be, but you need to be very careful. When you port forward, you're basically opening a door directly from the internet to your Pi. This means any service you expose, like SSH or a web server, could be found by others. So, you absolutely must use strong passwords, set up SSH keys, and keep your Pi's software updated. Think of it like making sure your house has really good locks if you're leaving a window slightly ajar.
Q2: What if my internet provider uses CGNAT?
If your internet service provider (ISP) uses Carrier-Grade NAT (CGNAT), it means you don't have a unique public IP address, so traditional port forwarding won't work. In this situation, cloud-based tunneling services like Ngrok or Dataplicity, or even setting up a reverse SSH tunnel to a public server, are your best bets. These methods work because your Pi initiates an outbound connection, which bypasses the CGNAT issue entirely. It's a bit like sending a message out rather than waiting for one to come in.
Q3: Can I control multiple Raspberry Pis behind one router?
Absolutely! You can control several Raspberry Pis behind a single router. If you're using port forwarding, each Pi would need a static local IP address, and you'd forward different external ports to different internal ports on each Pi. For example, external port 2222 could go to Pi A's SSH (port 22), and external port 2223 could go to Pi B's SSH (port 22). If you use a VPN, once you connect to your home VPN, you'll be able to access all your Pis by their local IP addresses, which is honestly very convenient. Cloud services often let you manage multiple devices from a single dashboard too. You can find more details on IoT device management on our site.
- Lol Superman Lost Media
- Lebron Kids
- Elsa Age
- Clifford Beaver Brandi Passante
- Did Camilla Go To Dianas Funeral
IoT Using Raspberry Pi - Pianalytix - Build Real-World Tech Projects
IOT Home Automation Using Raspberry Pi

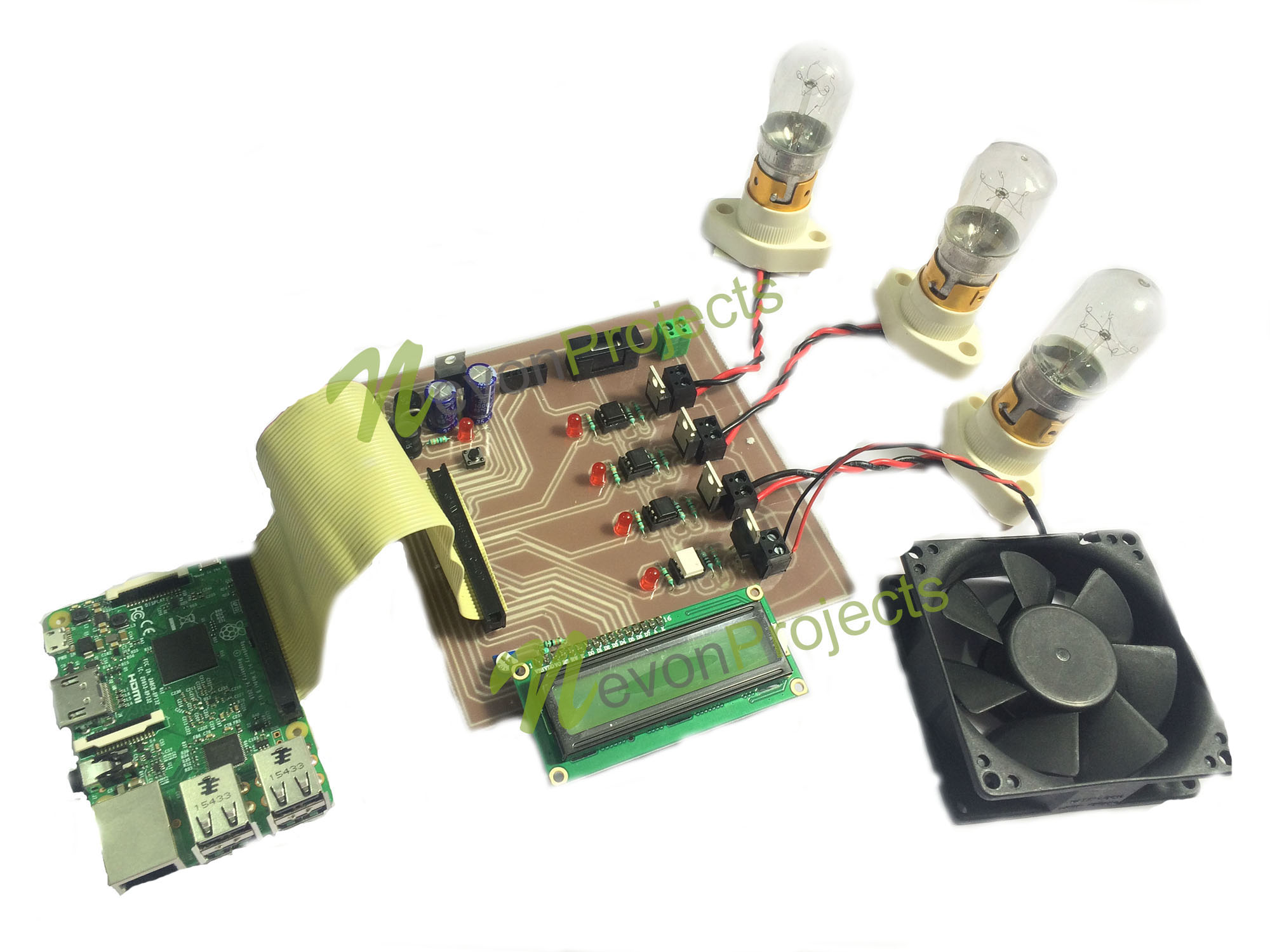
IOT Industry Automation Using Raspberry Pi